HELD for RANSOM
ISSUE 100 | VOLUME 8 | August 2021
RANSOMWARE is a long-standing problem and a growing national security threat. Tackling this challenge requires collaboration across every level of government, the private sector and communities.
Ransomware is a type of malicious software, or malware, that encrypts data on a computer making it unusable. A malicious cybercriminal holds the data hostage until the ransom is paid. If the ransom is not paid, the victim’s data remains unavailable. Cybercriminals may also pressure victims to pay the ransom by threatening to destroy the victim’s data or to release it to the public.
Cybersecurity Ventures has predicted ransomware will cost companies $20 billion worldwide in 2021. The U.S. Department of Justice reported that roughly $350 million in ransom was paid to malicious cyber actors in 2020, a more than 300 percent increase from the previous year. According to the 2020 Internet Crime Report, the FBI received 2,474 complaints identified as ransomware with adjusted losses of over $29.1 million last year. These losses do not include estimates of lost business, time, wages, files or equipment, or any third-party remediation services acquired by a victim. In some cases, victims do not report any loss amount to the FBI, thereby creating an artificially low overall ransomware loss rate. Lastly, the number only represents what victims report to the FBI via the IC3 and does not account for victim direct reporting to FBI field offices/agents.
There have already been multiple notable ransomware attacks in 2021, and despite making up roughly 75% of all ransomware cases, attacks on small businesses often go unnoticed. Like most cyberattacks, ransomware exploits the weakest link—employees—and many small businesses have yet to adequately protect their networks. About 90% of cyberattacks begin with a phishing email, according to research from security software firm Trend Micro.
Cloud-hosting Vendor Suffers Ransomware Attack
Several municipalities have been hit over the past several years by ransomware attacks impacted access to public records and disrupted closings. The threat hit much closer to home when on July 16, Cloudstar, which is a cloud-hosting and data security provider to title and settlement companies, discovered it was the victim of a highly sophisticated ransomware attack. As of Aug. 10, Cloudstar remained offline as the company continued to work with Tetra Defense, a third-party forensics company in recovery efforts.
Cloudstar President Chris Cury said the company continued to advance restoration efforts and anticipated recovering the majority of its customers’ data.
“Nevertheless, this process is very complex, and due to the extensive impact that this event had on our systems we are unable to provide a definitive ETA (for recovery),” he said. “We expect that this overall process will take several weeks with continued diligent effort. That said, we are continuing to work directly with individual customers to answer their questions and facilitate the return of their data when it is safe to do so.”
Cloudstar operates six data centers in the United States, serving more than 42,000 users.
Several software vendors and title companies offered their expertise and services to help ensure deals continue to close.
Shawn Fox, director of sales and marketing for Premier One, said his company helped Cloudstar clients get set up in the Microsoft Azure cloud platform. SoftPro, RamQuest and Qualia also stepped up to assist title companies get set up in their systems.
“Unfortunately, these companies did not have any of their data since the backups were affected in this attack as well,” Fox said. “We set them up with a blank database of the production software to get them operational. If a title company had not made any plans and were just hoping that Cloudstar came back, they would not be able to process any orders. A lot of the customers also had their emails hosted with Cloudstar, so they were also having a hard time with communication.”
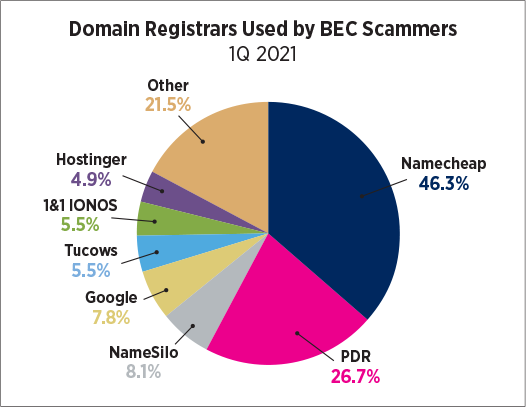
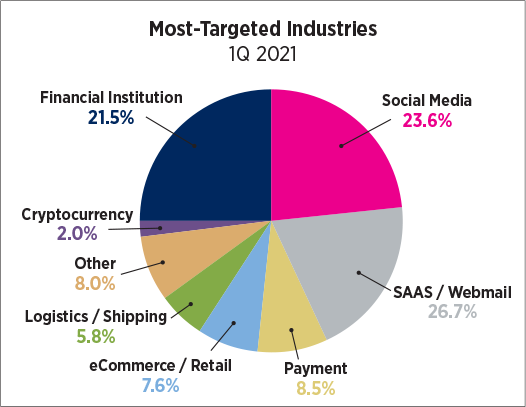
Fox said impacted title and settlement companies should contact regulators in the states they conduct business. The same companies also should contact their cyber insurance providers.
Kevin Nincehelser, chief operating officer for Premier One, informed affected title companies to focus on the minimum viable product, a version of a software with just enough features to be usable. This is core to any business continuity plan.
Nincehelser encouraged agents to verify their security status and ensure there was not an active threat to IT assets. Title companies should restore email communications with access to their domain registrar and Domain Name System (DNS) account, such as GoDaddy. Nincehelser said this can be completed quickly utilizing Microsoft 365.
“Title companies should restore their ability to process new orders,” he added. “This can be accomplished by obtaining a new instance of their production software on-premises or hosted with an available vendor such as Premier One, OP2, SoftPro or Qualia. Companies also must rebuild production processes and workflows. For many agents, the extensive customization to their production software will be lost. It’s best to begin rebuilding as soon as possible.”
If available, affected title and settlement companies should restore data if available or check with Cloudstar to access any data that was backed up.
Additionally, Nincehelser said companies should initiate legal and compliance protocols because many states have strict consumer reporting timelines.
“Evaluating this immediately is critical to staying in compliance with those timelines,” he said.
The Cloudstar incident is like a sophisticated attack in July on U.S. information technology firm Kaseya, where hackers demanded $70 million to unlock thousands of businesses affected by the hack. This attack was carried out through a vulnerability in software that helps businesses manage their computer systems, according to reports. Kaseya sells its software to large managed service providers, who in turn, help small and midsize businesses monitor and control their computer networks.
“This is one of the ripple effects that leads to riptide events,” said Karen Koogler, CEO of the Koogler Group. “Most business owners are unaware of the full extent of liability to which their businesses are exposed.”
From a liability perspective, Koogler said whether a company performs tasks in-house or outsources them to third-party providers, an organization is responsible for any loss or damage arising from unmanaged or improperly managed risk.
The federal Graham-Leach-Bliley Act (GLBA) requires financial institutions—including title and settlement companies—to protect consumer nonpublic personal information. Third-party contractors must also comply with the GLBA. The ALTA Title Insurance and Settlement Company Best Practices builds on this privacy framework to provide additional guidance.
While the Federal Trade Commission is the primary privacy and data security enforcer, many states have data privacy laws and regulations.
“It is essential to identify those with whom or through whom you do business, especially critical-service or high-risk providers whose actions have a major impact on your ability to conduct business,” Koogler said.

